Tuesday, July 2, 2013
PBS LA2: S05.1 Written Assignment
LA2.S05.1
Construct:S05 Current and Future Development of Open Source Software and the Latest
Development in ICT
Aspect: LA2.S05.1
Explain the latest open source software available and the latest development in ICT Instrument:
Written Assignment :
Task-
Candidate works in groups of 2 to 4 to conduct study AND / OR for discussion.
Written assignment MUST be done individually.
Refer to WAF.CW.LA2.S05.1
Suggested duration: 1-2 weeks
Values: • Appreciate • Cooperate • Confident
CONTENTS:
1. Explain the latest open source OS.
a. Meaning
b. TWO examples
2. Explain the latest open source application software.
a. Meaning
b. TWO examples
3. Explain the latest development in ICT.
a. ONE hardware
b. ONE software
4. Explain pervasive computing.
a. Meaning b. TWO examples
4. Follow required written assignment format.
a. Content format
b. Document format (Font: Arial, Size:12 ,Spacing:1.5)
6. Display cooperation.
a. Write the names of group members.
b. Verbal verification from group members or assessor’s observation.
TOTAL MARK: 20
Construct:S05 Current and Future Development of Open Source Software and the Latest
Development in ICT
Aspect: LA2.S05.1
Explain the latest open source software available and the latest development in ICT Instrument:
Written Assignment :
Task-
Candidate works in groups of 2 to 4 to conduct study AND / OR for discussion.
Written assignment MUST be done individually.
Refer to WAF.CW.LA2.S05.1
Suggested duration: 1-2 weeks
Values: • Appreciate • Cooperate • Confident
CONTENTS:
1. Explain the latest open source OS.
a. Meaning
b. TWO examples
2. Explain the latest open source application software.
a. Meaning
b. TWO examples
3. Explain the latest development in ICT.
a. ONE hardware
b. ONE software
4. Explain pervasive computing.
a. Meaning b. TWO examples
4. Follow required written assignment format.
a. Content format
b. Document format (Font: Arial, Size:12 ,Spacing:1.5)
6. Display cooperation.
a. Write the names of group members.
b. Verbal verification from group members or assessor’s observation.
TOTAL MARK: 20
Thursday, April 18, 2013
Lesson 30: Computer Software
Open Source & Proprietary Software discussion
Students should be able to distinguish.
Sunday, April 7, 2013
Lesson 29 : LA2.2 Hardware
GENERAL DEFINITION
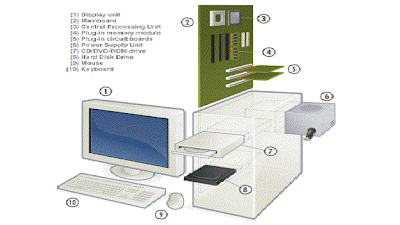
Computer hardware refers to the physical parts of a computer and related devices.
Internal hardware devices include
hard drives, and
RAM.
External hardware devices include
keyboards,
mouse(mice),
printers,
and scanners.
The internal hardware parts of a computer are often referred to as components, while external hardware devices are usually called peripherals. Together, they all fall under the category of computer hardware.
Sunday, March 31, 2013
Lesson 28: Clock Speed
Overview: Hertz is the term to describe 1 cycle per second of the computer process.
(http://www.techterms.com) Amazing Computer & Technology Term In The InternetA clock cycle, or simply a "cycle," is a single electronic pulse of a CPU. During each cycle, a CPU can perform a basic operation such as fetching an instruction, accessing memory, or writing data. Since only simple commands can be performed during each cycle, most CPU processes require multiple clock cycles.
In physics, the frequency of a signal is determined by cycles per second, or "hertz." Similarly, the frequency of a processor is measured in clock cycles per second. Since modern processors can complete millions of clock cycles every second, processor speeds are often measured in megahertz or gigahertz.
Frequency measures the number of times something occurs in a specific amount of time. For example, if someone visits the grocery store twice a week, her shopping frequency is 2 visits per week. While frequency can be used to measure the rate of any action, in technical applications it is typically used to measure wave rates or processing speed. These frequencies often occur multiple times per second and therefore are measured in hertz (Hz) or related units of measurement, such as megahertz or gigahertz.
One megahertz (abbreviated: MHz) is equal to 1,000 kilohertz, or 1,000,000 hertz. It can also be described as one million cycles per second. Megahertz is used to measure wave frequencies, as well as the speed of microprocessors.
Radio waves, which are used for both radio and TV broadcasts, are typically measured in megahertz. For example, FM radio stations broadcast their signals between 88 and 108 MHz. When you tune to 93.7 on your radio, the station is broadcasting at a frequency of 93.7 MHz.
Megahertz is also used to measure processor clock speeds. This measurement indicates how many instruction cycles per second a processor can perform. While the clock speeds of processors in mobile devices and other small electronics are still measured in megahertz, modern computer processors are typically measured in gigahertz.
Abbreviation: MHz.
Clock speed is the rate at which a processor can complete a processing cycle. It is typically measured in megahertz or gigahertz. One megahertz is equal to one million cycles per second, while one gigahertz equals one billion cycles per second. This means a 1.8 GHz processor has twice the clock speed of a 900 MHz processor.However, it is important to note that a 1.8 GHz CPU is not necessarily twice as fast as a 900 MHz CPU. This is because different processors often use different architectures.
For example, one processor may require more clock cycles to complete a multiplication instruction than another processor. If the 1.8 GHz CPU can complete a multiplication instruction in 4 cycles, while the 900 MHz CPU takes 7 cycles, the 1.8 GHz processor will be more than twice as fast as the 900 MHz processor. Conversely, if the 1.8 GHz processor takes more cycles to perform the instruction, it will be less than 2x as fast as the 900 MHz processor.
Other factors, such as a computer's bus speed, cache size, speed of the RAM, and hard drive speed also contribute to the overall performance of the machine. Therefore, while the processor's clock speed is a significant indicator of how fast a computer is, it is not the only factor that matters.
Lesson 27: Data Measurement
BYTES to BITS conversion.
How many megabytes in 1 GB?
MEASUREMENT CHART
(http://www.wu.ece.ufl.edu/links/dataRate/DataMeasurementChart.html)
NOTE: A lowercase "b" is used as an abbreviation for bits, while an uppercase "B" represents bytes. This is an important distinction, since a byte is 8x as large as a bit.
For example, 100 KB (kilobytes) = 800 Kb (kilobits).
How many megabytes in 1 GB?
MEASUREMENT CHART
(http://www.wu.ece.ufl.edu/links/dataRate/DataMeasurementChart.html)
| Unit | Value | Size |
|---|---|---|
| bit (b) | 0 or 1 | 1/8 of a byte |
| byte (B) | 8 bits | 1 byte |
| kilobyte (KB) | 10001 bytes | 1,000 bytes |
| megabyte (MB) | 10002 bytes | 1,000,000 bytes |
| gigabyte (GB) | 10003 bytes | 1,000,000,000 bytes |
| terabyte (TB) | 10004 bytes | 1,000,000,000,000 bytes |
| petabyte (PB) | 10005 bytes | 1,000,000,000,000,000 bytes |
| exabyte (EB) | 10006 bytes | 1,000,000,000,000,000,000 bytes |
| zettabyte (ZB) | 10007 bytes | 1,000,000,000,000,000,000,000 bytes |
| yottabyte (YB) | 10008 bytes | 1,000,000,000,000,000,000,000,000 bytes |
NOTE: A lowercase "b" is used as an abbreviation for bits, while an uppercase "B" represents bytes. This is an important distinction, since a byte is 8x as large as a bit.
For example, 100 KB (kilobytes) = 800 Kb (kilobits).
Lesson 26: Binary Coding
Binary code: ASCII "Ass Kee"
(http://www.telacommunications.com/nutshell/ascii.htm#chart)
ASCII, pronounced "ask-ee" is the acronym for
American Standard Code for Information Interchange. It's a set of characters which,
unlike the characters in word processing documents, allow no special formatting
like different fonts, bold, underlined or italic text. All the characters used
in email messages are ASCII characters and so are all the characters used in
HTML documents. (Web browsers read the ASCII characters between angle brackets,
"<" and ">", to interpret how to format and display HTML documents.)
An "ASCII file" is a data or
text file that contains only characters coded from the standard ASCII character set.
Characters 0 through 127 comprise the Standard ASCII Set and characters
128 to 255 are considered to be in the
Extended ASCII Set.
These codes, however, may not be the same in all computers and files containing these
characters may not display or convert properly by another ASCII program.
Knowing something about ASCII can be helpful.
ASCII files can be used as a common denominator for data conversions. For example,
if program A can't convert its data to the format of program B, but
both programs can input and output ASCII files, the conversion may be possible.
ASCII characters are the ones used to send and receive email. If you're familiar
with email, you already know that formatting like italic type and underlines are
not possible. Email transmissions are limited to ASCII characters and because
of that, graphics files and documents with non-ASCII characters created in
word processers, spreadsheet or database programs must be "ASCII-fied" and
sent as email file attachments. When the files reach
their destination they are "deASCII-fied" (i.e. decoded) and therefore,
reconstructed to restore them for use.
| ASCII | Description | ||
| 0 | NUL | Null | |
| 1 | SOH | Start of heading | |
| 2 | STX | Start of text | |
| 3 | ETX | End of text | |
| 4 | EOT | End of transmit | |
| 5 | ENQ | Enquiry |
| 64 | @ | ||
| 65 | A | ||
| 66 | B | ||
| 67 | C | ||
| 68 | D | ||
| 69 | E | ||
| 70 | F | ||
| 71 | G | ||
| 72 | H | ||
| 73 | I | ||
| 74 | J | ||
| 75 | K | ||
| 76 | L | ||
| 77 | M | ||
| 78 | N | ||
| 79 | O | ||
| 80 | P | ||
| 81 | Q | ||
| 82 | R | ||
| 83 | S | ||
| 84 | T | ||
| 85 | U | ||
| 86 | V | ||
| 87 | W | ||
| 88 | X | ||
| 89 | Y | ||
| 90 | Z |
(http://www.telacommunications.com/nutshell/ascii.htm)
Lesson 25: Data Representation
( http://www.willamette.edu/~gorr/classes/cs130/lectures/data_rep.htm)
Data Representation refers to the methods used internally to represent information stored in a computer. Computers store lots of different types of information:
How can a sequence of 0's and 1's represent things as diverse as your photograph, your favorite song, a recent movie, and your term paper?
It all depends on how we interpret the information. Computers use numeric codes to represent all the information they store. These codes are similar to those you may have used as a child to encrypt secret notes: let 1 stand for A, 2 stand for B, etc. With this code, any written message can be represented numerically. The codes used by computers are a bit more sophisticated, and they are based on the binary number system (base two) instead of the more familiar (for the moment, at least!) decimal system. Computers use a variety of different codes. Some are used for numbers, others for text, and still others for sound and graphics.
In ASCII, an "A" is 65," B" is 66, "a" is 97, "b" is 98, and so forth. When you save a file as "plain text", it is stored using ASCII. ASCII format uses 1 byte per character 1 byte gives only 256 (128 standard and 128 non-standard) possible characters The code value for any character can be converted to base 2, so any written message made up of ASCII characters can be converted to a string of 0's and 1's.
Forum :
x86 = 32bit
x64 = 64bit
"As the x86 term became common after the introduction of the 80386, it usually implies a binary compatibility with the 32-bit instruction set of the 80386. This may sometimes be emphasized as x86-32 to distinguish it either from the original 16-bit x86-16 or from the newer 64-bit x86-64 (also called x64). Although most x86-processors used in new personal computers and servers have 64-bit capabilities, to avoid compatibility problems with older computers or systems, the term x86-64 is often used to denote 64-bit software, with the term x86 implying only 32-bit.
Go with the 32bit... It has more compatible drivers and support. Unless you are going to be doing 3D Rendering, Video Editing, or RAW Files in Photoshop, 64bit OSs aren't worth the trouble."
Summary:
Smallest data representation is called BIT.
8 BITS is equal to 1 BYTES
ASCII uses 7 BITS to represent each character.
Data Representation refers to the methods used internally to represent information stored in a computer. Computers store lots of different types of information:
- numbers
- text
- graphics of many varieties (stills, video, animation)
- sound
How can a sequence of 0's and 1's represent things as diverse as your photograph, your favorite song, a recent movie, and your term paper?
It all depends on how we interpret the information. Computers use numeric codes to represent all the information they store. These codes are similar to those you may have used as a child to encrypt secret notes: let 1 stand for A, 2 stand for B, etc. With this code, any written message can be represented numerically. The codes used by computers are a bit more sophisticated, and they are based on the binary number system (base two) instead of the more familiar (for the moment, at least!) decimal system. Computers use a variety of different codes. Some are used for numbers, others for text, and still others for sound and graphics.
THE RELATIONSHIP BETWEEN BITS,BYTES & CHARACTER
- Memory consists of bits (0 or 1)
- a single bit can represent two pieces of information
- bytes (=8 bits)
- a single byte can represent 256 = 2x2x2x2x2x2x2x2 = 28 pieces of information
- words (=2,4, or 8 bytes)
- a 2 byte word can represent 2562 pieces of information (approximately 65 thousand).
- Byte addressable - each byte has its own address.
In ASCII, an "A" is 65," B" is 66, "a" is 97, "b" is 98, and so forth. When you save a file as "plain text", it is stored using ASCII. ASCII format uses 1 byte per character 1 byte gives only 256 (128 standard and 128 non-standard) possible characters The code value for any character can be converted to base 2, so any written message made up of ASCII characters can be converted to a string of 0's and 1's.
Forum :
x86 = 32bit
x64 = 64bit
"As the x86 term became common after the introduction of the 80386, it usually implies a binary compatibility with the 32-bit instruction set of the 80386. This may sometimes be emphasized as x86-32 to distinguish it either from the original 16-bit x86-16 or from the newer 64-bit x86-64 (also called x64). Although most x86-processors used in new personal computers and servers have 64-bit capabilities, to avoid compatibility problems with older computers or systems, the term x86-64 is often used to denote 64-bit software, with the term x86 implying only 32-bit.
Go with the 32bit... It has more compatible drivers and support. Unless you are going to be doing 3D Rendering, Video Editing, or RAW Files in Photoshop, 64bit OSs aren't worth the trouble."
Summary:
Smallest data representation is called BIT.
8 BITS is equal to 1 BYTES
ASCII uses 7 BITS to represent each character.
Lesson 24: Overview of computer system
Keywords:
Computer System is defined as combination of several units or component to process information.
There are INPUT, OUTPUT, PROCESS & STORAGE as the main components in computer system.
In order for this system to function it must involved hardware, software and users.
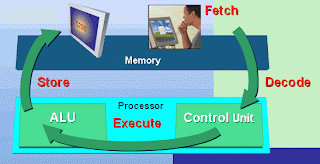
The computer process is involved ; Fetching-Decoding-Execute-Store.
Bit is the smallest data representation which has only TWO conditions 1
JUST THE FACTS
Date: 5 Apr 2013 Class: 4A
Methods: Lecture, discussion & simple task
Materials: Power point notes
Rating : Good! Student can explain the process "A is pressed and displayed on screen"
Computer System is defined as combination of several units or component to process information.
There are INPUT, OUTPUT, PROCESS & STORAGE as the main components in computer system.
The computer process is involved ; Fetching-Decoding-Execute-Store.
Bit is the smallest data representation which has only TWO conditions 1
JUST THE FACTS
- Computers work by running programs or software. Programs are normally stored on your hard disk and loaded into memory to be executed by the CPU.
- You control the operating system through its user interface. A GUI or graphical user interface uses the manipulation of visual components, while a command line interface requires you to type in specific commands.
- Your computer has two kinds of software: systems software (aka the operating system), which is loaded when your computer starts up, and applications which are programs you use to accompish a particular task.
- Computer programmers create programs by writing source code in a programming language. This source code must be converted to a native machine language that the CPU can execute.
- Your CPU consists of two parts—the Control Unit and the Arithmetic Logic Unit (ALU)— that work together to perform the steps of the machine cycle: fetch, decode, execute, and store.
- Just like numbers, pixels and sounds, your computer stores computer programs as binary numbers. In the end, "bits is bits".
Date: 5 Apr 2013 Class: 4A
Methods: Lecture, discussion & simple task
Materials: Power point notes
Rating : Good! Student can explain the process "A is pressed and displayed on screen"
Thursday, February 21, 2013
Learning Area #2: COMPUTER SYSTEM
Topics in this chapter;
2.1 System Concept
2.2 Hardware
2.3 Software
2.4 Installation
2.5 Current & Future Development
Saturday, February 2, 2013
Tuesday, January 29, 2013
PBS: S01.1
School Based Assessment (PBS)
Learning Area: LA1-Information Communication & Technology
Topic: Security Measures(Lesson 19)
Activity 1
S01.1 Apply correct security procedures using antivirus.
STEPS:
1. Choose antivirus software to be used.
2. Start the antivirus software and select area to be scanned.
3. Scan the selected area. List the name(s) of the virus detected.
4. Choose and apply any or all of the following when a virus is detected - delete/remove, clean/heal, quarantine/move to vault.
Activity 2
S01.2 Apply correct security procedures using spyware.
STEPS:
1. Choose anti-spyware software to be used.
2. Start the anti-spyware software and select area to be scanned.
3. Scan the selected area. List the name(s) of the spyware detected.
4. Choose and apply any or all of the following when a spyware is detected - delete/remove, clean/heal, quarantine/move to vault.
Worksheet 2: Lesson 6-10
Lesson 6:
1.
What is ethics?
I.
A study about moral principles.
II.
A custom that guides human behaviour.
III.
A regulation that must be obeyed by the public.
IV.
A knowledge about what is good and what is bad.
A.
I, II and III
B.
I, II and IV
C.
I, III and IV
D.
II, III and IV
2.
Which of the following statements shows the impact of using a company’s
computer without authorisation?
I.
Decreasing company’s expense.
II.
Increasing the company’s expense.
III.
Improvement in term of staff personal skills.
IV.
Creating an unhealthy relationship
between
employer and worker.
A.
I and II
B.
II and III
C.
II and IV
D.
III and IV
3.
Which of the following statements shows against the code of conduct in
computing?
A.
Accessing the computer without authorisation.
B.
Using the computer to create useful computer codes.
C.
Using the original computer software from legal vendors.
D.
Using computer knowledge to contribute to human life.
Task: Identify Ethics & Law
- Main objective is to produce ethical computer users, who uses computer to do good things.
- Universal, can be applied anywhere all over the world.
- As a rule to control computer users.
- To prevent computer users from doing any action that is referred to as computer misuse.
- Judged by judicial standards.
- Depends on country and state where the crime is committed.
- As a guideline to computer users.
- Judged by moral standards.
Lesson 15: Computer Crime
OVERVIEW
What are Computer Crimes?
Computer FRAUD.............................................................................................................................
Copyright infringement......................................................................................................................
Computer Theft and...........................................................................................................................
Computer Attack................................................................................................................................
are considered as computer crimes. These activities are using computer or ICT application and that 100% illegal according to the Cyber Law.
Lesson 14: Cyber LAW
Synopsis
Cyber law refers to any laws relating to protecting the Internet and other online communication technologies.
Why Cyber Law is needed?
Concern of protecting the privacy of certain individual, intellectual property right and valuable information in the cyber world. Cyber Law may help people from any lost due to cyber crime or criminal acts done by the cyber criminals.
What are the Cyber Law in Malaysia?
1. Digital Signature Act 1997
2. Telemedicine Act 1997
3. Computer Crime Act 1997
4. Communication & Multimedia Act 1998
Drafted Cyber Law
1. Private Data Protection Bills
2. Electronic Government Activities Bills
3. Electronic Transactions Bills
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
Date: 21st Feb 2013
Class: 4B(12/14)
Resources: school local site http://10.192.230.90/sementanet/ictspm, PC, Projector, score A module.
Activities:
1. Revise the internet filtering method(Verbal discussion, in pairs)
2. Explanation on Cyber Law by the teacher.
3. Observe the video clip entitled " Facts of Cyber Crime "
4. In pairs: Give the reason why cyber law is needed?
5. Worksheet 1: Matching the correct Cyber Law in Malaysian
Rating : Very Good!
Date: 21st Feb 2013
Class: 4A(17/18)
Resources: school local site http://10.192.230.90/sementanet/ictspm, PC, Projector, score A module.
Activities:
1. Revise the internet filtering method(Verbal discussion, in pairs)
2. Explanation on Cyber Law by the teacher.
3. Observe the video clip entitled " Facts of Cyber Crime "
4. Homework & incoming presentation: Why Cyber Law is needed?
Rating: Very Good!
Lesson 13: Internet Filtering
Date: 18 Feb 13
Class: 4B ( 3 boys, 9 girsl)
Resources: ICT, F4 CD1, module score A, internet, powerpoint
Activities:
1. Conduct a simple research using internet - google
2. Find information on keyword blocking(group 1), web site rating(group 2), web filtering(group 3)
Date: 19 & 21 Feb 13
Class: 4A(18 Ss)
Resources: Score A module, school local site http://10.192.230.90/sementanet/ictspm
Activities:
1. Read and copy the notes from the module.
2. Answer 5 objectives question.
3. Discussion + Summary
Rating: good!
Keynotes:
Internet filtering approach is to prevent the controversial contents intruding our computer and privacy.
1. Keyword Blocking 2. Site Blocking 3. Web Rating Approach
Lesson 12: Controversial Contents
Date: 18 Feb 13
Class: 4B ( 3 boys, 9 girsl)
Resources: ICT, F4 CD1, Score A module, internet, powerpoint
Activities: cd exploring( contents, synopsis, summary)
Rating : good!
Date: 19 Feb 13
Class: 4A(18 Ss)
Resources: Score A module, school local site http://10.192.230.90/sementanet/ictspm
Activities: Self study & task given
Task:
1. Explain the meaning of controversial content in full sentences.
2. Give 3 impact of slander to the society.
Rating: can be improved!
Keynotes:
Controversial Issues - Popular facts or cases that give impact to the community.
Controversial content in ICT are any materials or information that content violence, pornography and slander.
Pornography : exploitation of human sexual behavior that can lead to social problem and low moral attitude in the society!
Slander : spreading lies and rumors in order to make the other party fall or destroyed!
Violence: War, Shooting, Fighting, Killing etc.
Lesson 11: Verification
DEFINITION
Verification is the act of proving or disproving the correctness of a system with respect to a certain formal specification.
There are two methods commonly used in verification, which are user identification and processed object. User identification refers to the process of validating the user. Processed object refers to something the user has such as identification card, security token and cell phone.
Verification is the act of proving or disproving the correctness of a system with respect to a certain formal specification.
There are two methods commonly used in verification, which are user identification and processed object. User identification refers to the process of validating the user. Processed object refers to something the user has such as identification card, security token and cell phone.
Lesson 10: Authentication
Definition
Authentication is the process of determining whether someone or
something is, in fact, who or what it is declared to be. In private and
public computer networks (including the Internet), authentication is
commonly done through the use of logon passwords.
The use of digital certificates issued and verified by a Certificate Authority (CA) as part of a public key infrastructure is considered likely to become the standard way to perform authentication on the Internet. Logically, authentication precedes authorization (although they may often seem to be combined).
Lesson 9: Privacy
Data and Information privacy.
Data: a collection of raw unprocessed facts, figures and symbols. Then, computer is used to process data into information. In general, data include texts, numbers, sounds, images and video.
Rights of individuals and companies to deny or restrict the collection and use of information about them.
Data & Information privacy are threaten through;
1. Electronic Profile
2. Cookies
3. Spyware
Privacy is needed because we don't want any part of our private and valuable information fall to other parties especially bad parties!
Monday, January 28, 2013
Lesson 8: Intellectual Property Rights
Hey..... where are the notes? Ok...why not we use the internet to find out about the terms below.
Your Task: WRITE THE INFORMATION USING COMMENT!
Group 1:State the definition of Intellectual Property Rights
Group 2:What is Intellectual Property Law?
Group 3: What is Protected Invention?
Group 4: Patents for inventions & Trademarks for brand identity?
Group 5: Design for product appearance & Copyright for material?
Lesson 7 : Differences between Ethics & Law
ETHICS
GUIDELINE: As a guideline to computer users.
MORAL STANDARDS: Ethical behavior standards is judged by moral.
FREE TO FOLLOW: Computer users are free or ignore the code of ethics.
NO PUNISHMENTS: No punishment for anyone who ignore ethics.
UNIVERSALS: can be applied anywhere, all over the world.
PRODUCE ETHICAL COMPUTER: To produce ethical computer users.
USERS IMMORAL: Not honoring computer ethics means ignoring the moral elements(immoral).
LAWS
CONTROL: As a rule to control computer users.
JUDICIAL STANDARDS: Law is judged by judicial standards.
MUST FOLLOW: Computer users must follow the regulations and law.
PENALTIES, IMPRISONMENTS AND OTHER PUNISHMENTS: Penalties, imprisonments and punishments for those who break the law.
DEPENDS ON COUNTRY: Depends on country and state where the crime is committed.
PREVENT MISUSING OF COMPUTERS: To prevent misuse of computers.
CRIME Not honoring the law means committing a crime.
GUIDELINE: As a guideline to computer users.
MORAL STANDARDS: Ethical behavior standards is judged by moral.
FREE TO FOLLOW: Computer users are free or ignore the code of ethics.
NO PUNISHMENTS: No punishment for anyone who ignore ethics.
UNIVERSALS: can be applied anywhere, all over the world.
PRODUCE ETHICAL COMPUTER: To produce ethical computer users.
USERS IMMORAL: Not honoring computer ethics means ignoring the moral elements(immoral).
LAWS
CONTROL: As a rule to control computer users.
JUDICIAL STANDARDS: Law is judged by judicial standards.
MUST FOLLOW: Computer users must follow the regulations and law.
PENALTIES, IMPRISONMENTS AND OTHER PUNISHMENTS: Penalties, imprisonments and punishments for those who break the law.
DEPENDS ON COUNTRY: Depends on country and state where the crime is committed.
PREVENT MISUSING OF COMPUTERS: To prevent misuse of computers.
CRIME Not honoring the law means committing a crime.
Lesson 6: Computer Ethics & Legal Issues
THE TEN COMMANDMENTS OF COMPUTER ETHICS(USA)
1. You shall not use a computer to harm other people.
2. You shall not interfere with other people's computer work.
3. You shall not snoop around in other people's computer files.
4. You shall not use a computer to steal.
5. You shall not use a computer to bear false witness.
6. You shall not copy or use proprietary software for which you
have not paid.
7. You shall not use other people's computer resources without
authorization or proper compensation.
8. You shall not appropriate other people's intellectual output.
9. You shall think about the social consequences of the program
you are writing or the system you are designing.
10. You shall always use a computer in ways that ensure
consideration and respect
REVIEW(COMMENTS)
1. Define ETHICS in general.
2. State TWO examples of ethical computer ethics.
3. State TWO examples of unethical computer ethics.
1. You shall not use a computer to harm other people.
2. You shall not interfere with other people's computer work.
3. You shall not snoop around in other people's computer files.
4. You shall not use a computer to steal.
5. You shall not use a computer to bear false witness.
6. You shall not copy or use proprietary software for which you
have not paid.
7. You shall not use other people's computer resources without
authorization or proper compensation.
8. You shall not appropriate other people's intellectual output.
9. You shall think about the social consequences of the program
you are writing or the system you are designing.
10. You shall always use a computer in ways that ensure
consideration and respect
REVIEW(COMMENTS)
1. Define ETHICS in general.
2. State TWO examples of ethical computer ethics.
3. State TWO examples of unethical computer ethics.
Worksheet 1: Lesson 1-5
Lesson 3:
1.
A bank clerk transfers money into your account. This transaction is stored in
the
_____________.
A.
workstation
B.
supercomputer
C.
embedded computer
D.
mainframe computer
2.
____________ uses computers to experiment new graphic designs with possible
interiors.
A.
An artist
B.
A scientist
C.
An architect
D.
A researcher
3.
Customers benefit from Electronic Banking in terms of:
I.
24 hours service
II.
Electronic Fund Transfer
III.
Electronic Cash Deposits
IV.
Electronic Loan Application
A.
I, II, and III
B.
I, II, and IV
C.
I, III, and IV
D.
I, II, III, and IV
4.
Teachers benefit from the use of computers in schools because computers…
I.
weaken learning
II.
can enhance interactive learning
III.
can be used as an effective teaching aids
IV.
can strengthen cognitive development
A.
I and III
B.
II and III
C.
II, III, and IV
D.
I, II, III, and IV
Lesson 5:
1.
Using computers frequently and for long hours is not harmful.
A.
TRUE
B.
FALSE
2.
The usage of ICT technologies such as to create pornographic websites can have
a negative
impact
on the society.
A.
TRUE
B.
FALSE
3.
We can only find limited sources of information on the internet.
A.
TRUE
B.
FALSE
4.
The cost of using the internet is more expensive compared to other modes of
communication.
A.
TRUE
B.
FALSE
5.
With the internet, the interaction among societies is unlimited.
A.
TRUE
B.
FALSE
6.
Using ICT technologies can create a paperless office environment.
A.
TRUE
B.
FALSE
7.
It takes ages for someone to receive information through the internet.
A.
TRUE
B.
FALSE
8.
ICT brings positive changes to the society’s lifestyle.
A.
TRUE
B.
FALSE
9.
Normally the “computer error” is caused by the machine itself.
A.
TRUE
B.
FALSE
10.
There is only one way of communication through ICT technology and that is via
Yahoo!
Messenger.
A.
TRUE
B.
FALSE
Lesson 5: The Impact Of ICT To Society
REVIEW THIS!
POSITIVE IMPACTS
1. Faster Communication Speed
2. Low Communication Cost
3. Paperless Environment
4. Reliable Mode of transportation
NEGATIVE IMPACTS
1. Fraud
2. Pornography
3. Hacking
4. Identity Theft
5. Social Problems
6. Health Problems.
POSITIVE IMPACTS
1. Faster Communication Speed
2. Low Communication Cost
3. Paperless Environment
4. Reliable Mode of transportation
NEGATIVE IMPACTS
1. Fraud
2. Pornography
3. Hacking
4. Identity Theft
5. Social Problems
6. Health Problems.
Lesson 4: Computerized & Non Computerized
REVIEW THIS!
BANKING SYSTEM
Before ICT
...................................................................................................
...................................................................................................
With ICT
...................................................................................................
...................................................................................................
SUMMARY
Computerized System
- Use electricity
- Faster & reliable
- Good Productivity
Non Computerized System
- Manually, electricity is not compulsory
- Slow & not so reliable
- Less productivity
BANKING SYSTEM
Before ICT
...................................................................................................
...................................................................................................
With ICT
...................................................................................................
...................................................................................................
SUMMARY
Computerized System
- Use electricity
- Faster & reliable
- Good Productivity
Non Computerized System
- Manually, electricity is not compulsory
- Slow & not so reliable
- Less productivity
Subscribe to:
Comments (Atom)